An Overview of Kerberos
Kerberos is a complex system with many parts. To get a good understanding of Kerberos, it is important to understand the different software components that underlie the whole system.
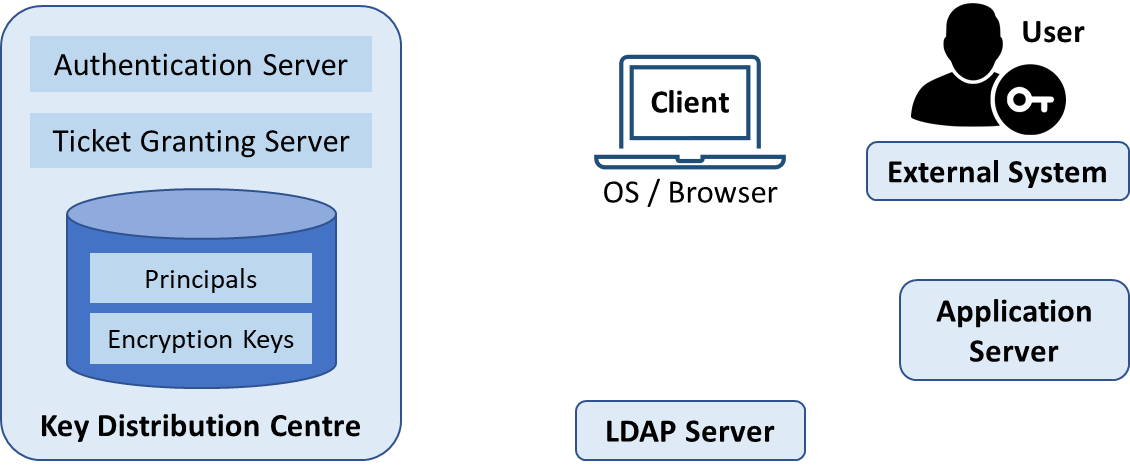
Components in a KDC and some common systems in a Kerberos Realm
The Key Distribution Centre
In a Kerberos Realm, the Key Distribution Centre (KDC) plays a central part in accepting user logins and generating tickets for such logins.
It consists of 3 logical components:
a database of all principals and their associated encryption keys
the Authentication server
the Ticket Granting Server
In a given realm, there must be at least one KDC.
A KDC also stores additional information for each principal in its database, such as password lifetimes, last password change and more.
The Authentication Server
The Authentication Server (AS) issues an encrypted Ticket Granting Ticket (TGT) to clients who wishes to “login in” to the Kerberos realm.
The client does not have to prove its identity to the KDC; instead, the TGT that is sent back to the client is encrypted with the user’s password. Since only the user and the KDC know the user’s password, when the login process attempts to decrypt the ticket using the password supplied by the user, only the correct password will correctly decrypt the ticket.
The TGT returned by the Authentication Server can then be used, once decrypted by the client, to request individual service tickets from the Ticket Granting Server.
The Ticket Granting Server
The Ticket Granting Server (TGS) is used to request for service tickets of other systems in the same realm.
The TGS issues individual service tickets on client requests. This is different and not to be confused with the TGT.
The TGS takes two pieces of data from the requesting client:
A ticket request that includes the principal name representing the service the client wishes to contact.
A TGT that has been issued by the Authentication Server.
The TGS verifies that the TGT is valid by checking to ensure that it is encrypted with the KDC’s TGT key, and then issues the client with the requested service ticket.
Tickets
A Kerberos ticket is an encrypted data structure issued by the KDC that includes a shared encryption key that is unique for each session.
It also contains a flag that indicates if the ticket can be forwarded to another service, along with other fields.
Tickets serve two purposes: to confirm identity of the end participants, and to establish a short-lived encryption key that both parties can share for secure communication (called session keys).
The main fields that a ticket contains are:
The requesting principal name (the user’s principal)
The service’s principal name
When the ticket becomes valid and when it expires
A list of IP addresses that the ticket can be used for
A shared secret encryption key (session key) for user/application communication.
Keytab
The keytab (short for “key table”) stores the long-term keys for one or more principals. Keytabs are often used to allow server applications to accept authentications from clients. They can also be used to obtain initial credentials for client applications.
In Kerberized services, the service’s keytab contains a principal’s encrypted key and the key version number. When a client authenticates itself with such a service, the service reads the ticket contents sent by clients for authentication, both the encrypted key and the key version number (kvno) and checks that it matches with its keytab entry for the client.
A keytab contains one or more entries, where each entry consists of a time stamp (indicating when the entry was written to the keytab), a principal name, a key version number, an encryption type, and the encryption key itself.
Although the keytab may contain one or more entries, it usually only contains one entry.
A keytab can be displayed using the
klistcommand with the-koption.The keytab file is a binary file which follows this format.