Kerberos Sequence Diagrams
High Level Authentication Flow
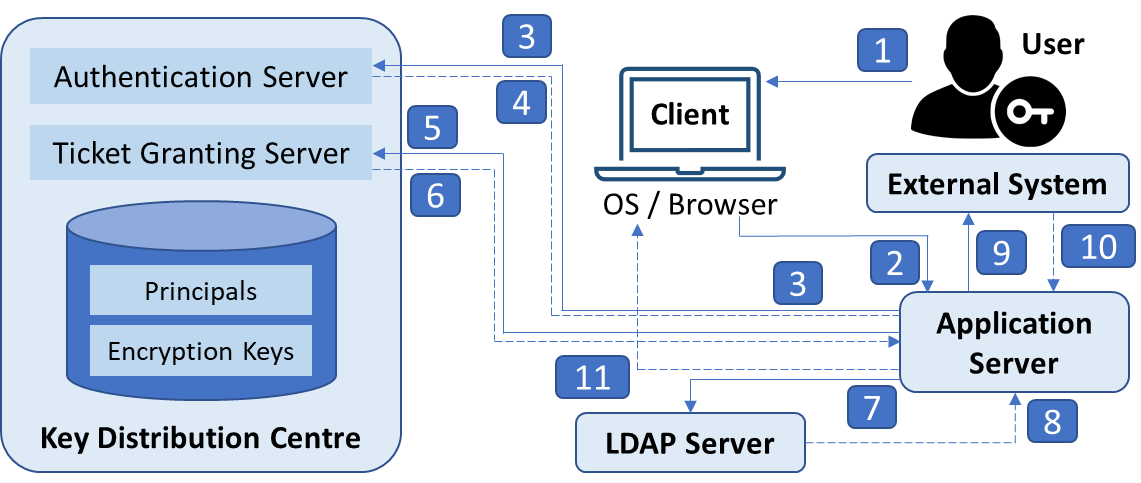
The diagram above shows the different systems involved in a typical authentication and authorisation flow.
The user logins on his PC. This login client could either be an application on the OS, the Windows OS or a internet browser.
In the case of login on the browser to a web application, the call would be redirected to an application server. In the initial setup, since no previous valid TGT is available, a 401 Unauthorized is returned. Otherwise, if a valid TGT exists, we skip to step 5.
Assuming no valid TGT exists, the application server requests a TGT from the Authentication Server of the KDC.
With a valid user name and password, the Authentication Server returns a valid TGT. At this point, the Application Server has authenticated the user and can use the TGT for further authentications.
To connect to other secure systems in the realm, the Application Server presents the KDC with the TGT and a ticket request. This ticket request includes the principal name of the service(s) that it wishes to connect to.
The TGS verfies the TGT and issues a service ticket as requested back to the Application Server.
The Application Server can then requests the user’s authority list, possibly from an LDAP Server, using the service ticket.
The LDAP Server returns the user’s list of authorities, which indicate what functions they are authorised to access.
The Application Server can connect to an external system if it has a valid service ticket for that system.
The Application Server then makes the authorised function call to the external system
It then returns the results to the Client, completing the operation requested by the client with Single Sign On.