Networking
Ingress Types
Ref: https://kubernetes.io/docs/concepts/services-networking/ingress/#ingress-controllers
Single Service Ingress
Simple fan out
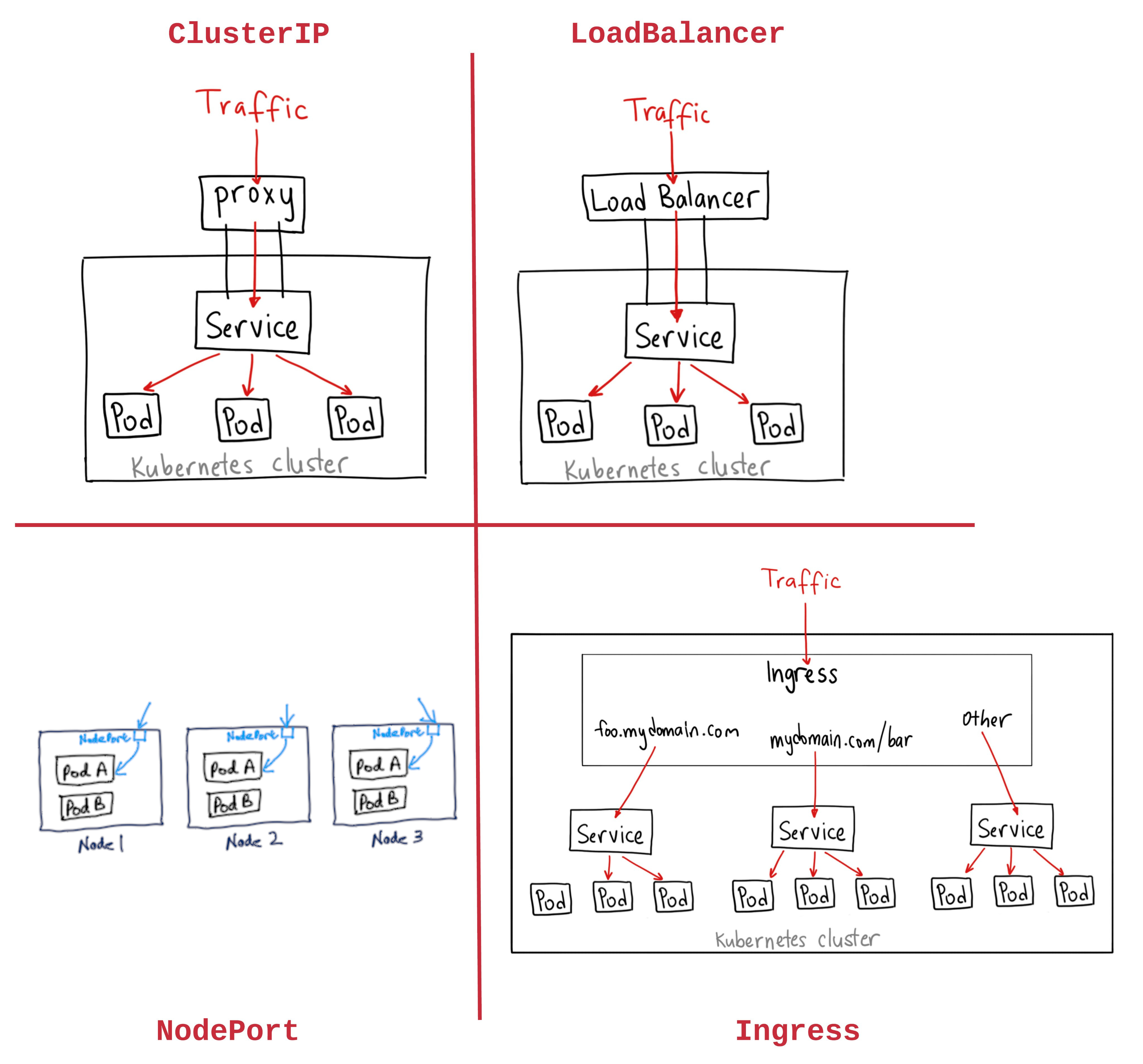
Kubernetes calls its HTTP(S) based load-balancing system Ingress as it operates at Layer 7 of the OSI stack.
Service object
A Kubernetes service object operates at Layer 4 of the OSI stack, i.e. TCP and UDP level and is hence unaware of the content of these TCP packets.
Network Policies
Kubernetes network policies work similar to network firewalls. With Kubernetes network policies, you specify how groups of pods are allowed to communicate with each other and other network endpoints.
It uses labels to select pods and defines rules to specify what traffic is allowed to the selected pods.
The
policyTypesareingressand / oregress. They provide whitelisted rules to explicitly allow traffic in or out of the pod from other pods and endpoints. Thus, all other traffic is blocked except for these whitelisted rules.There are three kinds of selectors that can be specified for ingress and egress network types. They are:
podSelector: to specify which pods the ingress and / or egress refers should be applied to.
namespaceSelector: namespace object resource header for pod selector criteria
ipBlock: to specify which network these external pods may be residing on.
Note that are enforced the network solution implemented on the cluster. Flannel does not support network policies.
For examples and usage, see Network Policy yaml
Liveness Probe
The three kinds of liveness probes supported by Kubernetes are:
HTTP GET
TCP connection
Exec probe