LUKS Storage Device Encryption
LUKS1
The Linux Unified Key Setup (LUKS) encryption was developed to provide a standard passpharse key setup process with the ability to use multiple passwords or passphrases. It is used to encrypt block devices, i.e. storage devices such as SSDs and hard disks.
Your password or passphrase is used with a key to encrypt a master key, which is used with symmetric encryption / decryption on the data that is stored on the disk. This encryption approach is similar to that used by GPG. This approach is commonly known as the KEM/DEM paradigm. The Key Encapsulation Method/Data Encapsulation Method is the standard method of using a public key to encrypt something.
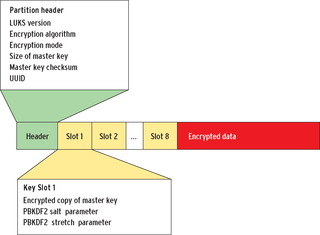
An encrypted storage device showing the LUKS header, 8 slot keys and encrypted data.
Each slot key contains a master key encrypted with your password. The eight key slots in LUKS are eight different encryptions of the same MasterSecretKey under eight different passwords.
LUKS2
One of the common problem with LUKS (version 1) is damage to the LUKS header stored at the start of the partiton. This header stores the metadata described above, required for encryption / decryption.
LUKS2 provides the a number of improvements over LUKS1. The more important ones are:
The improved LUKS2 extends LUKS1’s ability by storing this metadata with redundancy, so that there is a much greater chance of recovery in case the metadata becomes corrupted.
LUKS2 also provides more flexibility by allowing the metadata to be stored externally for use by integration tools. With the detached header, the encrypted device contains no visible or detectable metadata. This new format also provides an easy way to backup the whole LUKS2 header.
The number of keyslots are only limited by the provided header size area. Keyslots also have priorities. Keyslots can be marked for use only if explicity specified, e.g. as a recovery keyslot.
Using LUKS
Installation and Setup
The easiest way to use LUKS is to install the cryptsetup package. The following commands show how they can be installed on the more common Linux distros:
Debian, Ubuntu:
$ sudo apt install cryptsetupCentOS, Fedora, RedHat:
$ sudo dnf install cryptsetupArch Linux, Manjaro:
$ sudo pacman -S cryptsetup
Find out the partition to be encrypted with $ sudo fdisk -l
In my example, I will be encrypting the SD card on /dev/mmcblk0.
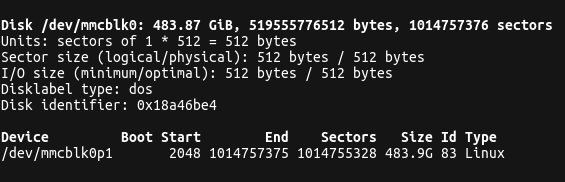
Example of fdisk -l output showing the SD card details
Encryption of device
We now encrypt the /dev/mmblk0 partition with the following command:
sudo cryptsetup --type luks2 luksFormat /dev/mmcblk0
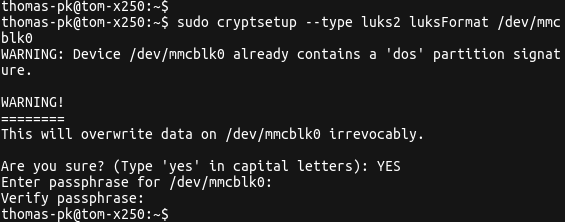
Encrypting a device with cryptsetup
As shown in the screenshot above, the command requires you provide a password, which is verified before proceeding with encryption of the device.
We are using the newer LUKS2 format which reduces our change from the LUKS header being corrupted and rendering the whole device unusable.
Mapping the Decrypted device
Before we can use the encrypted device, we need to create its decrypted block device and map this new handle to the /dev/mapper folder before it can be used by any Linux applications.
This is done with the open action. In our case, we execute the following command:
sudo cryptsetup open /dev/mmcblk0 encrypted-sd
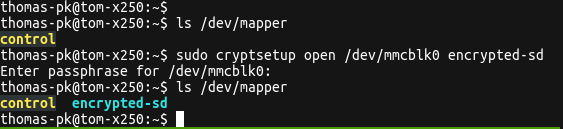
Creating the decrypted mapping device for normal use
As can be seen from the screenshot above, we have chosen to call the new handle encrypted-sd which now appears under the /dev/mapper folder. Notice how the command asks use for the password / passphrase which is required to decrypt the data. We can now use this handle to perform normal Linux operations as if it was a usual block or storage device.
Formatting the encrypted device
We now format the mapped device with the following command:
sudo mkfs.ext4 /dev/mapper/encrypted-sd
Formatting the mapped decrypted device
This now create the usual ext4 filesystem onto the mapped device.
Normal Use
Mounting
Before you can mount the device, please ensure you have created a mapped entry of the decrypted block device with the
openaction of the cryptsetup command. See the previous section on how to do this.We use the usual
mountcommand to access the mapped device to a folder:
$ sudo mount -t ext4 /dev/mapper/encrypted-sd /mnt
Mounting the mapped device to a folder
We can now access the folder as if it were a normal device. The encryption is transparent to applications that access the device through the folder.
Unmount and Close
After we have used the device, we unmount it the normal way.
It is very important to use the
closeaction of the cryptsetup command once we have finished using the device, so that it cannot be used without the password.
$ sudo umount /mnt$ sudo cryptsetup close encrypted-sd